Understanding the Authentication and Authorization process
Overview
Passpack views itself as the data steward to your sensitive information and goes to great lengths to ensure your information is completely secured against intrusion or leakages from the Passpack Password Manager. The first step in protecting access to your sensitive information is ensuring we can establish an identity of the person accessing information (Authentication) and then verifying the rights and sharing to that individual are enforced (Authorization).
Authentication
The key objective in authentication is establishing an identity of the person or system accessing Passpack. We provide multiple methods to authenticate, and, in that process, we have several steps which may be required to fully pass the authentication process.
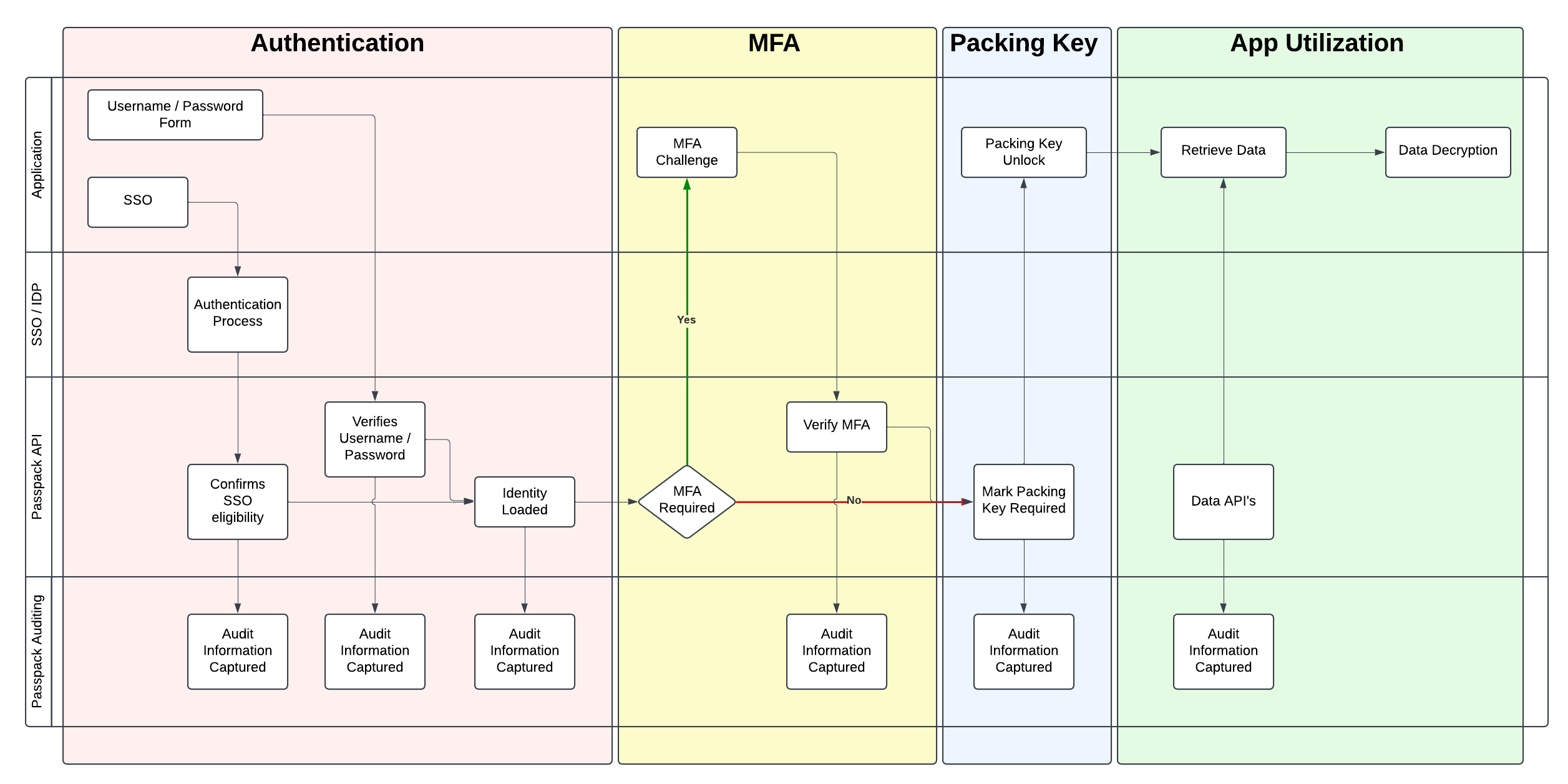
The steps involved in authenticating a user and allowing them to decode data are:
- Authentication
- MFA
- Packing Key
The following flow diagram illustrates a high level, simplified process. Further information is found following the diagram.
We will use an analogy of returning to an apartment building after an absence to correlate the Passpack process with steps we routinely perform. While not a perfect analogy we hope it helps to illustrate the concepts.
Authentication
A user has two choices when authenticating to to the Passpack API - Username / Password or SSO. The purpose of this step is to locate correlate a registered user within the system with the request to access data.
Username / Password is the simplest method and does not rely on any third party solutions. It is, however, "another password" to remember which is why we also support SSO.
SSO does rely on third party solutions such as Google and Azure to authenticate a user. These systems may or may not require MFA verification and have varying degrees of sophistication depending on how they are configured. Once the SSO login is authenticated the provider communicates directly to Passpack that the user is authenticated and who they have authenticated as.
An important aspect of this step is that the username / password or SSO step has some degree of risk in that the username / password may be stolen or the computer hacked and an existing SSO session is used to try to access your Passpack account. We provide further risk mitigation due to lost / compromised credentials by proceeding to the next step.
Analogy: This step is like entering an apartment building outer door. You could use a key to open the door, a key code, or other methods such as an RFID card. You are inside the first door but you are not yet inside your apartment. Sometimes these keys, codes, or RFID cards are lost and may be picked up by a random person who may now impersonate you and access the apartment complex.
MFA (Multi Factor Authentication)
Multi Factor Authentication is a methodology where you posess some piece of information which is typically more secure and stored in a separate location than your username / password. The MFA solutions supported by Passpack are intended to be on your person and have a freshness guage - time plays an important aspect in the validity of the MFA code you are using.
Currently, TOTP providers (Google Authenticator, Microsoft Authenticator, or other TOTP tools) and hardware based Yubikey tokens are supported by Passpack.
Analogy: Depending on how your apartment building is configured you may only be within a common area of the complex. You are not yet inside your apartment and must now open your door. The MFA is the door lock and is sophisticated such that it only unlocks with a code generated on your phone or by putting a device into an USB slot. Both devices generate codes which expire so even if you walk up to your door and a passerby distracts you and sees your code they could not use that code in the future to gain access to your apartment.
Packing Key
The final step to get access to your sensitive data is to enter your Packing Key. (Please see the key concept: Packing Key). Only after this data is entered may the system be in a state where you can securely decrypt your data.
Analogy: Once you enter your apartment you have an alarm that has been triggered. You must enter a code to disable / bypass.
Authorization
Once identity has been confirmed and validity checked then Passpack performs many steps to ensure that the data which is requested is authorized for your use.
This means that Passpack uses the identity to:
- Generate the password list and make available password details
- Generate the team list and team details
- Inform the application the user's rights and permissions within the app. For example, if the user is an administrator they may be able to invite new team members.
Audit Information: Passpack captures audit information so that we can establish how the system is behaving. We capture identifiers such as "12345678" which may represent a user and "99911231" which may represent a password. An audit record correlates an action with identifiers so that we can log a statement such as:
User 12345678 deleted password 99911231 on 1/1/25.
We do not have the ability to capture decrypted password / team information as we do not have the required encryption material. This information is secured even from Passpack personnel. Your organization admins are the only ones who can generate audit reports that replace the password identifier with a decrypted name.