Packing Key Bypass
Overview
Key Concepts: Packing Key, Registered Device, Authentication / Authorization
While the most protection is achieved through the consistent utilization of a packing key to unlock your sensitive data it is also possible to remove this step and streamline the authentication / authorization process. Please read more on our approach to the authentication / authorization process so that you may understand the issues related to bypassing a packing key.
Prerequisites
Before you can configure your account to bypass entering a packing key you must meet the following requirements.
- You must be on the proper subscription level.
- Your organization must allow device registrations.
- Your organization must allow packing key bypass.
- Each device you wish to utilize the bypass process must be enrolled individually.
If your subscription level downgrades to a tier not supported by this feature your account will be required to enter a packing key upon login regardless of prior enrollment status.
Changes to the Login Flow
When a user attempts to access Passpack a login workflow is initiated containing stepwise authentication and authorization steps. The Packing Key Bypass capability only alters the "Packing Key" step; a user must still adhere and meet the regular "Authentication" and "MFA" login requirements configured for their account. For example, if an account is configured to require an MFA code then the user must enter an MFA code before the Packing Key Bypass capability is triggered.
Below is a simplified diagram indicating the flow change:
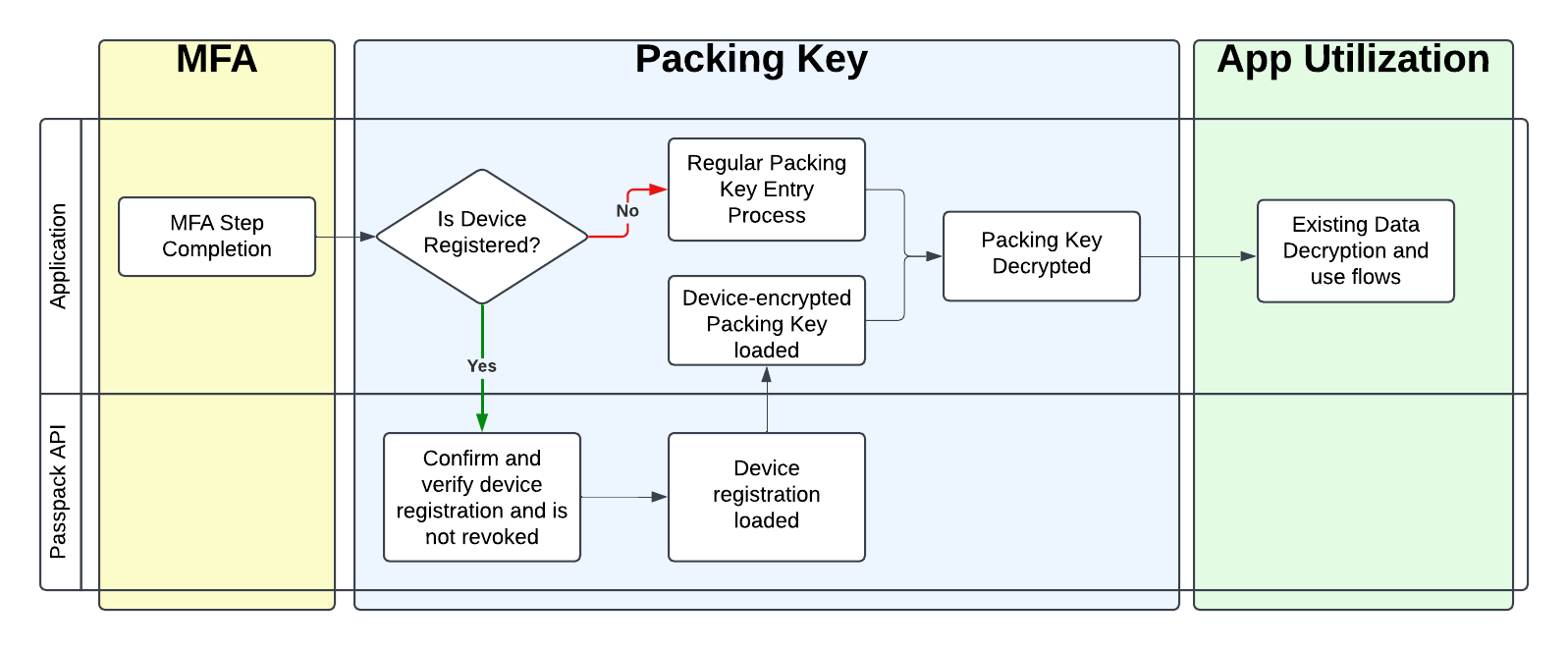
While enabling this capability may lead to fewer steps in the login workflow it does transfer some of the security from the user to a trusted device. Trust may be fluid in the world of ever evolving threats, and it is the user's responsibility manage those threats. The Packing Key Passphrase is intended to be a piece of information that only the user is capable of entering. We highly recommend ensuring your computer always applies security updates for the operating system and browser application as guided by your organization security guidelines.
Technical Details and Approach
Fully enabling Packing Key Bypass on your account entails registering a device and then enabling that device registration to enable Packing Key Bypass.
Step 1. Device Registration
Please refer to the Device Registration Process for detailed information. You will not be able to proceed unless the device is registered.
Step 2. Enabling Packing Key Bypass
After the device has been registered the appropriate device-specific encryption material has been created which will support Packing Key Bypass.
Below is a logical flow of the enrollment process.
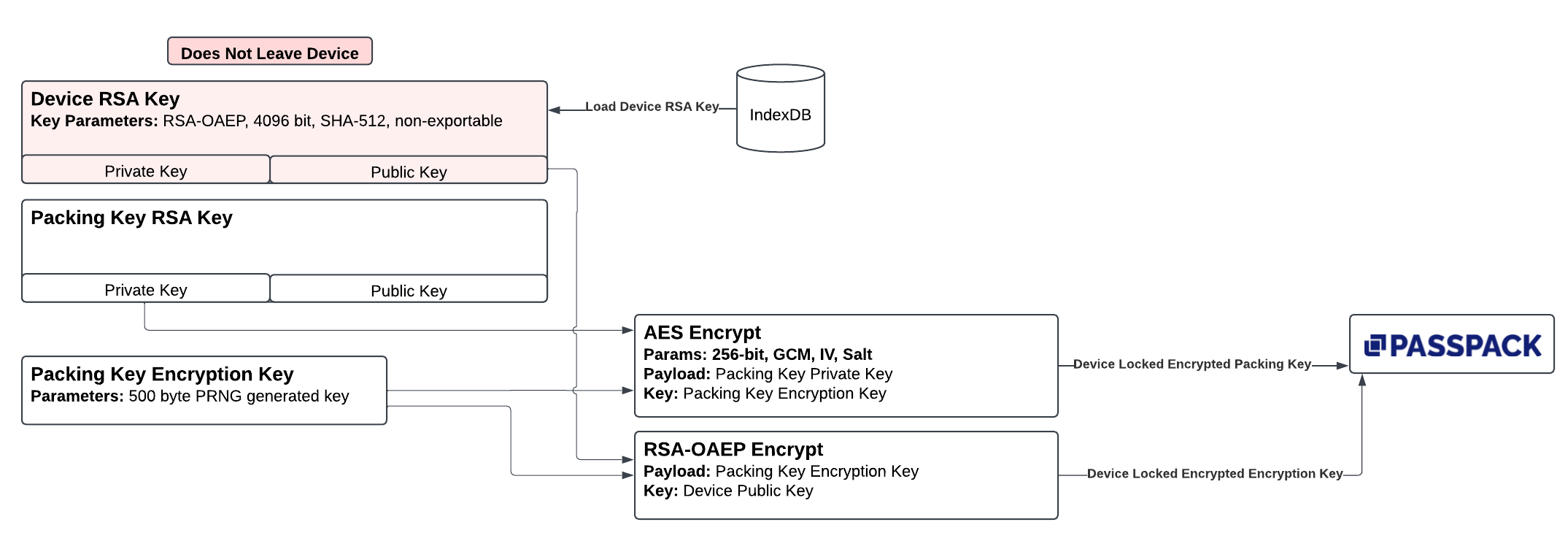
Description of Process
The user may enable Packing Key Bypass by navigating to Settings -> Security -> Devices . The user will be asked if they wish to enable the bypass functionality which performs the following steps:
- The
Device RSA Keyis retrieved from the browser's IndexDB. - One symmetrical key is generated using the cryptographically secure pseudorandom number generator within the browser. The keys are each 500 bytes long and are designated:
Packing Key Encryption Key- Used to encrypt the user'sPacking Key RSA Keyprivate portion of the RSA key.
- The
Packing Key RSA Keyprivate portion is AES encrypted withPacking Key Encryption Key. The encrypted result is securely stored in the Passpack API for secure distribution. This creates a device-locked version of the packing key. - The
Packing Key Encryption Keyis RSA encrypted using theDevice RSA Keyand is securely stored in the Passpack API.
Once the process completes no new data is stored locally in the IndexDB.
Step 3. Packing Key Bypass In Action
Once the device has been enrolled in the Packing Key Bypass the device is ready to execute a streamligned authentication and authorization flow the next login session.
Please remember - The bypass setting does not remove the need to log into the system nor enter an MFA, if required.
Below is a logical flow of the streamligned login process.
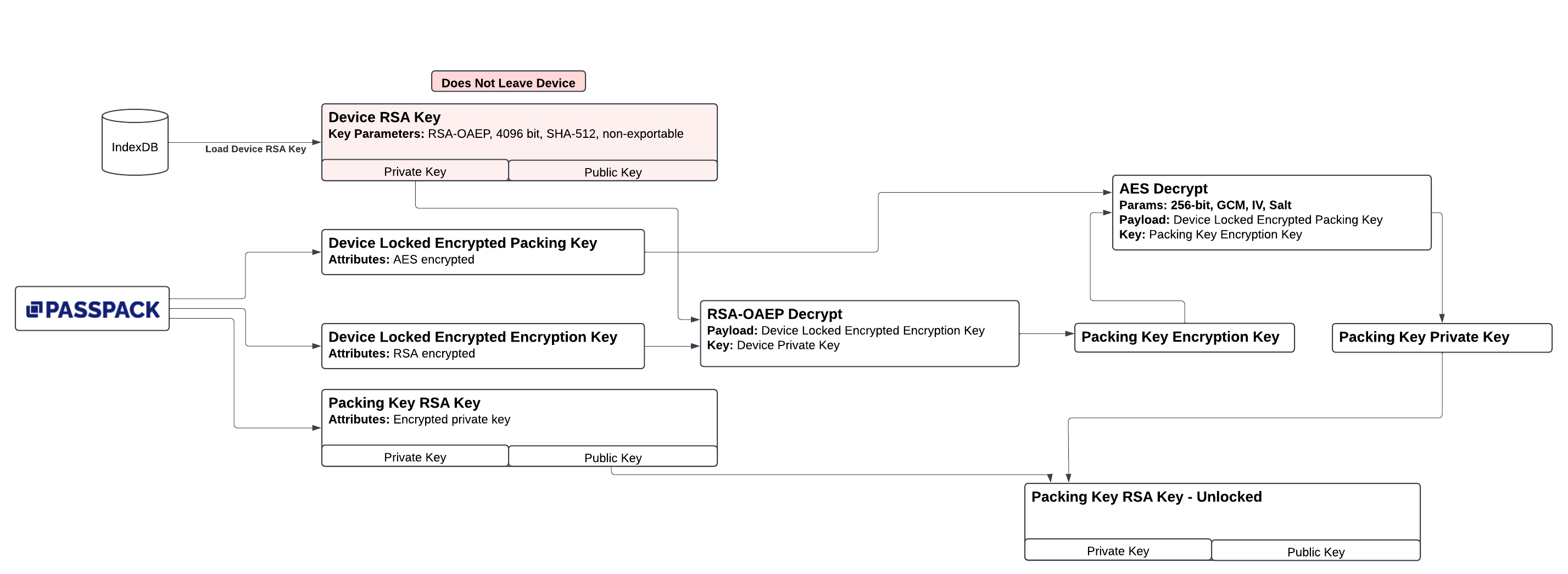
Description of Process
- The
Device RSA Keyis retrieved from the browser's IndexDB. - The browser sends a request to the server for several keys. Once authenticated the following keys are returned:
Device Locked Encrypted Packing Key Encryption KeyDevice Locked Encrypted Packing KeyPacking Key RSA Key- This is the user's RSA key used in both bypass mode and not. It has an encrypted private key and the required public key for later use.
- The
Device Locked Encrypted Packing Key Encryption Keyis decrypted using theDevice RSA Key. The decrypted result is thePacking Key Encryption Key. - The
Packing Key Encryption Keyis used to decrypt theDevice Locked Encrypted Packing Keyresulting in the private portion of the usersPacking Key RSA Key. - A new object is created in memory that combines the public portion of the
Packing Key RSA Keydownloaded from Passpack and the decrypted private portion of thePacking Key RSA Key. This keyset is then used to fully unlock the system.